MySQL is known for being easy to use and highly secure. That’s why it is the number one choice for many organizations, including the biggest brands like Facebook, Google, Uber, and YouTube. Because it’s open-source, it’s free to use and modify even for commercial purposes. But although it can be very secure, the security features are not always utilized properly.
Cybercriminals are good at finding ways to exploit the masses. Ransomware attacks have penetrated everything from cities, schools, and hospitals to large and small businesses. Victims are tricked to allow malicious programs into their systems where those programs lock files until getting ransom. Organizations of all kinds that use MySQL and other database management systems are at risk of attacks.
Targeting civic establishments in addition to businesses is a smart move for cybercriminals because our society will crumble without them. Knowing this, hackers take advantage of vulnerabilities in MySQL to make money from targets that have no leeway to refuse the ransom.
Ransomware is a lucrative industry for a cybercriminal, especially as we continue to rely on technology for storing all kinds of data in all sectors. Last year, some of the most damaging ransomware attacks successfully exploited targets for trillions of dollars. It is more crucial than ever to protect your database from unwanted access.
Ransomware Attacks
In 2020, the average ransom amount demanded in ransomware attacks had reached $170,000 per incident by Q3. Although criminals usually stick to their word and restore data once the ransom has been paid, it’s still impossible to know whether your data is completely safe after suffering an attack.
Such attacks have become more expected since Covid changed our digital landscape. Remote workers and businesses were forced to rely on cloud-based project tools and other types of online databases to collaborate with fellow team members, clients, and contractors. And while these kinds of tools do allow managers to set team permissions for control, such measures are not enough.
Complicating things further, more and more people of all digital expertise levels are utilizing online collaboration tools, and most of them are still not security-savvy. With so much information coming through different channels, it can be tough for even the most proficient users to define whether the data is from a legitimate source.
That’s why cybercriminals have been taking advantage of the fear and misinformation surrounding the pandemic. Malicious links embedded in things like fake CDC emails have been circulating. They exploit pandemic-related concerns by misrepresenting themselves with very convincing layouts and logos to trick recipients into letting the scammers right into their computers.
In 2021, hacker groups are becoming even more sophisticated and elusive in their tactics. Cryptocurrency is a popular format for ransoms. Crypto tracing capabilities are fairly new, and it is that much harder to catch cybercriminals. Private data becomes an increasingly valuable commodity.
PLEASE_READ_ME
One of the most elusive and dangerous attacks of the past year, now known as PLEASE_READ_ME, has changed the way we think about the scale and capabilities of ransomware technology. Most ransomware attacks are aimed at specific entities that have a lot to lose. This kind of targeted attack is usually well-planned and seamlessly executed, forcing the victims to pay top dollar to keep private data from being auctioned off.
The PLEASE_READ_ME attack, in contrast, was a more opportunistic exploit. It focused on targeting MySQL servers with weak credentials. Although they made less money per victim, a multitude of machines and MySQL databases were hacked with automated scripts. The attacks did not even use malware (just a script).
By the end of 2020, there were a total of 250,000 databases stolen in these attacks and sold on the dark web. The victims were asked to pay.08 BTC (the Bitcoin currency) to restore their databases, adding up to nearly $4,350 at Bitcoin’s current exchange rate.
This unprecedented attack has put users of MySQL on edge. We have learned that no one is safe, and we must ensure that credentials are secure.
Protecting MySQL Databases
In the light of the staggering success of PLEASE_READ_ME and other ransomware attacks based on weak credentials, SQL attacks are one of the most common forms of cyberattacks. It is time to ensure that your databases are protected from extortion.
Here are some steps you can take to fortify the security of your credentials and databases:
Deploy a Password Manager
Many security management tools can help with automated monitoring of the database and security protocols. Of course, every user must create a unique password, but it is not enough. Use the password management system that will require changing every password regularly.
For example, implement the password requirements, such as the number of digits, the presence of special characters, etc. Then, require updating this password every 60 days to a new password that has not been used in the past. This can help to keep your database users accountable and complicate the tasks for even experienced cybercriminals.
Use the Principle of Least Privilege
The principle of least privilege means you should only give users access to files that they need to complete the tasks required of them. In other words, not every employee needs full access to every database you manage. Use SQL server administration to control who has access to what.
Many tools manage database administration. You don’t have to go to the painstaking effort of keeping track of usernames, passwords, permissions, and assignments all on your own. By blocking off certain parts of the database, not only you make an attack less damaging, but also make it easier to track and pinpoint the vulnerability if the breach took place.
Incorporate Zero-trust Security Models
A zero-trust model assumes no identity can be trusted. Therefore, all users require authentication before getting access to data and other resources. In addition to not trusting human users, it is crucial to hold machines to the same zero-trust standards.
Automation technology is a fantastic investment for businesses of all kinds to increase efficiency, but trusting machine identities can pose serious issues. Using a real-time monitoring program and keeping track of user identities and their associated access and privileges are essential to maintaining an effective zero-trust policy.
SSL and TLS Encryption
Secure Sockets Layer (SSL) certificates are a good place to start when it comes to encrypting company data. It is wise to specify your SSL setting for each user.
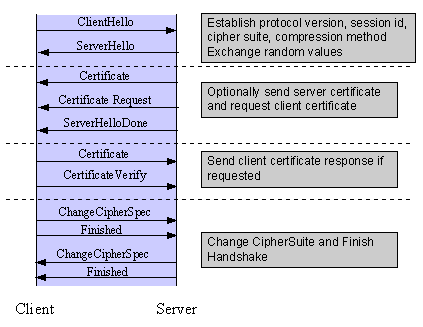
Your database should be encrypted, but it’s also important to encrypt the network and guarantee that any third parties with access also use encryption protocols. Remember that you’re only as secure as your weakest link.
Double-check that you have SSL or its successor, Transport Layer Security (TLS), enabled. Ask your third-party providers about the encryption protocols they have in place as well.
Remove Anonymous Users
When taking the above steps to increase authentication security, you should also delete any anonymous users or users without passwords. This will ensure that there are no doors left wide open for hackers to come in. It is very easy for a cybercriminal to log into your MySQL servers if you do not require a password.
Cybercriminals who are executing SQL attacks are well aware of all vulnerabilities in hardware and software, and especially security issues in the cloud. It’s how they make their living. An anonymous account can easily allow direct access to confidential files and other data.
Enable Audit Logging
Last but not least, make sure you have audited logging enabled. Audit logging keeps track of the time, date, and location of logins, as well as certain user activity. You can classify your SQL data so you know what is sensitive information.
This type of data management becomes critical when you experience a data breach or any kind of cyberattack. Then you can see when and how the attacker accessed your server and what data was affected. It’s also a good idea to have this log continuously monitored.
While automation is key to this process efficiency, it is also wise to have a person audit the logs and software to make sure that nothing slips through the cracks.
Protect Yourself Today
The digitization of the economy has created a breeding ground for cybercriminals to find new and more damaging ways to exploit people and businesses. In 2020, the cost of cyber ransoms increased by 336%, and that number is going up every day. Continued innovation in technology will inevitably lead to innovation in exploitation and data theft as well.
There will always be criminals to look out for, no matter the size of your business or how much data or money you have. Automated ransomware attacks and other cyber attacks work best when a wide net is cast. This means, for scammers, it’s not always about achieving the biggest heist. As we have learned from the ransomware trends of last years, a series of sneaky attacks that quietly shut down small businesses or civic organizations add up over time. Even when the pandemic becomes a bad memory, scammers will find other ways of duping the vulnerable into downloading malicious files.
In everyday life, we take certain precautions to protect ourselves from crime. Our activity on the internet should be no different. The trends indicate we can expect a continued rise in attempted and successful ransomware attacks in the future. Staying vigilant in monitoring your security protocols and putting into practice these tips will greatly reduce your chances of falling victim to damaging attacks.
In addition to implementing these guidelines, there are many tools available to assist you with MySQL database management. Use automation to your advantage to stay safe and maintain a balance between security and usability.










I simply want to tell you that I am new to blogging and site-building and seriously enjoyed this page. More than likely I’m likely to bookmark your blog post . You actually have good posts. Regards for sharing with us your blog site.