In this article, we are going to explore the Identity and Access Management concepts available in Amazon Web Services. Abbreviated as IAM, it enables AWS admins and users to control how services are available to other users within the account. In cloud computing, setting up the correct access for users is very important in order to control how the services are being accessed. In order to deal with such rules, AWS provides a service, known as Identity and Access Management, that can be used to define roles and policies. Then, users and groups can be created and granted specific access to resources as required.
As a pre-requisite, it is expected that you have an active subscription for an Amazon Web Services account and you are quite familiar with the services.
How to Use AWS IAM Portal
Once you have successfully created and logged in to your Amazon Web Services console, simply search for the keyword IAM in the search bar and service should be available.
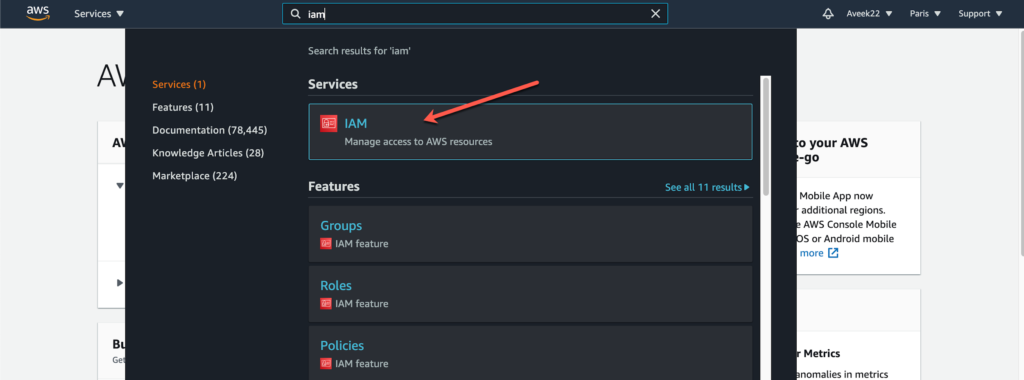
As you can see in the figure above, the IAM service appears as we search for it. Click the service to open it and proceed further.
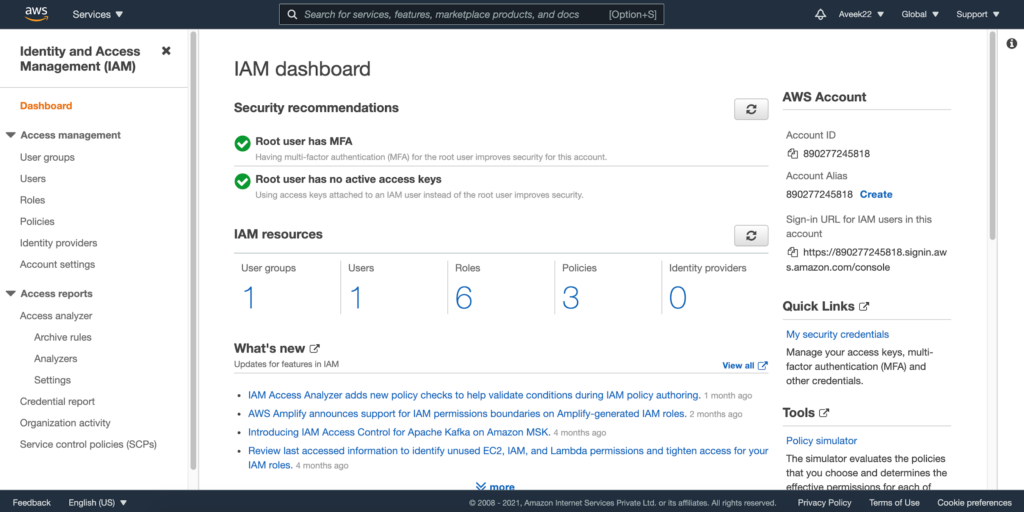
As you open the AWS IAM services from the search bar, the IAM dashboard appears. The IAM Dashboard is a consolidated view of all the activities that can be performed in AWS IAM. In the IAM Dashboard, you can configure all the activities required to control the access to the AWS resources and services.
Components of AWS IAM
Let us try to understand the basic concepts of using the AWS IAM service. There are four main components:
- Users – These are actual users that you can add to the IAM console. A user can be a developer, an administrator or a manager. Any person who would need to log in to the AWS console, has to have a valid user created in the IAM.
- User Groups – There might be cases when multiple users can have similar access to resources. In such cases, access can be defined at a group level and users can be added to those groups. All the users in the group will have the same access.
- Policies – Policies are statements or the rules that define what access is granted or denied to a specific user or a group. In AWS IAM, policies are written in JSON form that explicitly mentions the nature of access granted or revoked from the user.
- Roles – Roles are similar to policies, but these are applied to the AWS services instead of users of groups. For example, a role for an AWS Lambda function might define if it can read files from an S3 bucket or not.
We will explore each of the above four components in the next section.
Configure Users
As already mentioned, all individual users that need access to any of the services in the AWS console must be added as a user in IAM first. Users are typically of two types – Root user and IAM user. The root user belongs to the user who is responsible for creating the account. All other accounts that will be created later on are IAM users. A root user will have access to all the resources and services within the AWS service. However, for an AWS IAM user, access is limited and can be controlled using the policies.
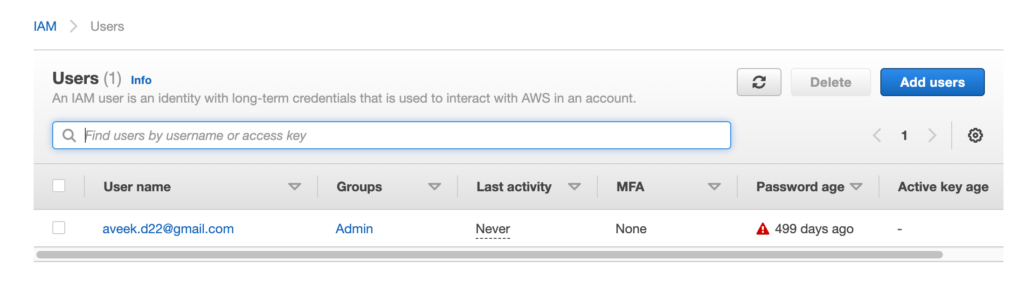
Configure User Groups
Groups are a logical collection of AWS IAM users that can have similar roles or access. This makes it easier for an administrator to control the access since the policies need to be defined only once and users can be added or removed from groups based on the conditions that apply. For example, a group can be comprised of developers, managers, testers, etc. such that all users in the group are assigned with similar access controls.
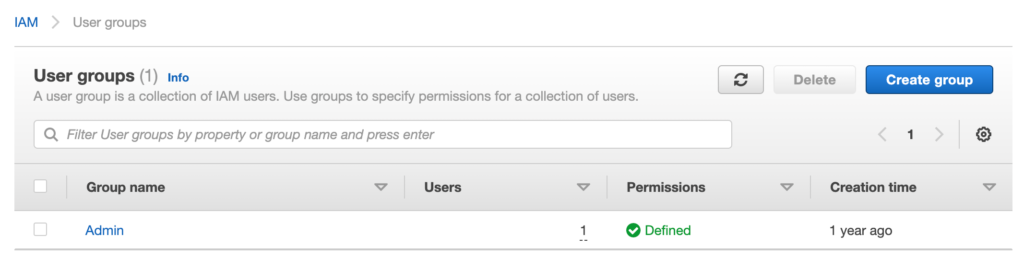
Setup Authorization
Now that we know about users and user groups, we can start digging deep with policies in AWS IAM. In AWS, all the resources are governed by policies to grant or deny access. As soon as a user requests access to any service or resource in AWS, the associated policies are evaluated first, and based on the policy, AWS allows or restricts the users to access the service. There are two types of policies within AWS.
- Identity based policies – These policies are attached directly to users or roles that allow them to access services and resources based on the policy. For example, a user trying to access a bucket in S3.
- Resource based policies – These policies define how AWS services granted access to other resources and services within AWS. For example, a Lambda function is trying to access a bucket in S3.
A policy in simple terms in just a JSON structure that defines a few rules as follows.
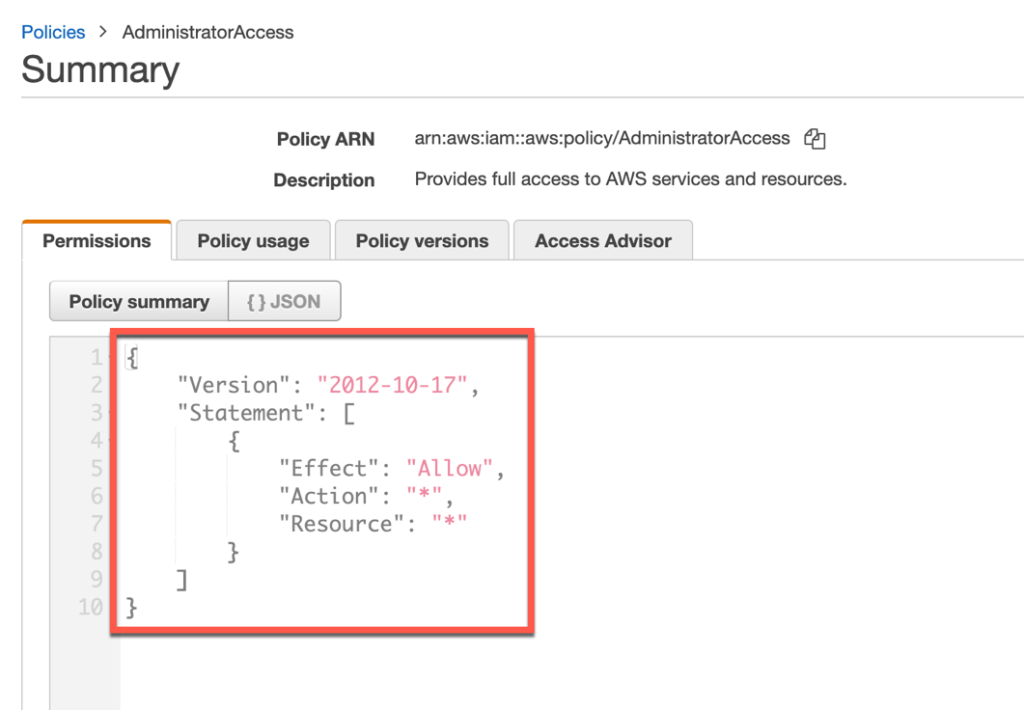
As you can see in the figure above, this policy allows access to all resources, as mentioned by the asterisk.
Configure Roles
In AWS, roles are similar to permissions but instead of granting permissions to users or groups, a role is rather associated with an AWS service itself. Let us consider the scenario in which we configure an EC2 instance that will read CSV files stored in S3 buckets, process them and store it into a database in RDS. The EC2 machine will need to have read access to the S3 buckets and also have read and write access to the RDS. For this, we cannot create another user to which policies can be attached. Hence, we can create a role for the EC2 machine and attach the policies to the role instead.
How to Create AWS IAM User
Now that we have some idea regarding the various objects available in AWS IAM, we can now go ahead and get some hands on. In this tutorial, we are going to create a user in IAM and then create a bucket in S3. We will also attach a policy that will allow the user to read and write files to the S3.
In order to proceed, let us navigate to IAM and click Users and then Add Users.
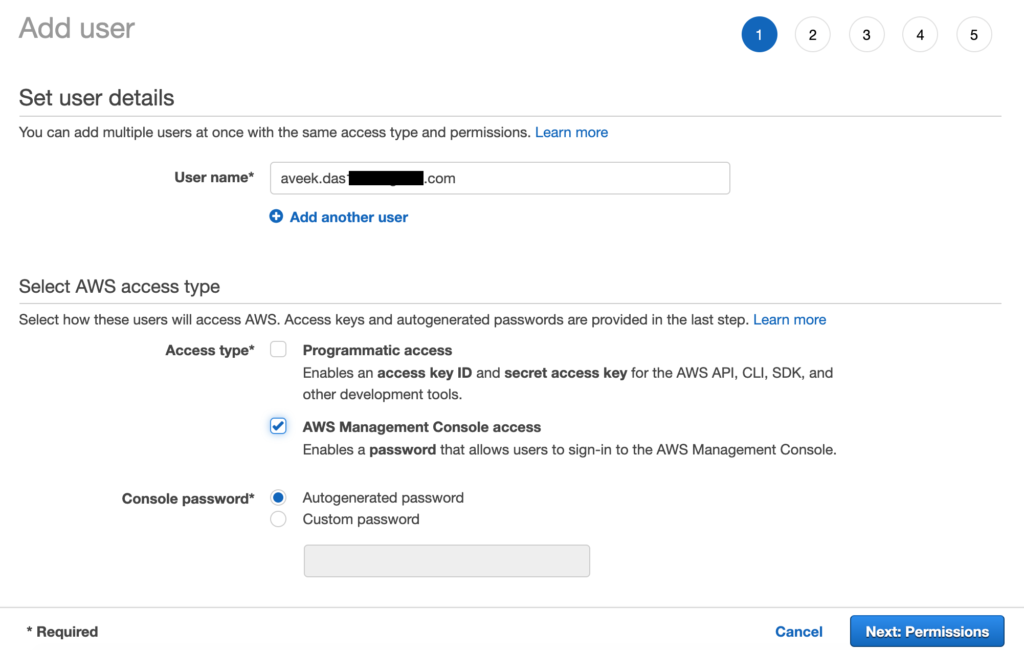
Here, you need to add a new user by providing their email address. Also, you can select the type of access that is allowed – Programmatic or Console. Click Next: Permissions to continue.
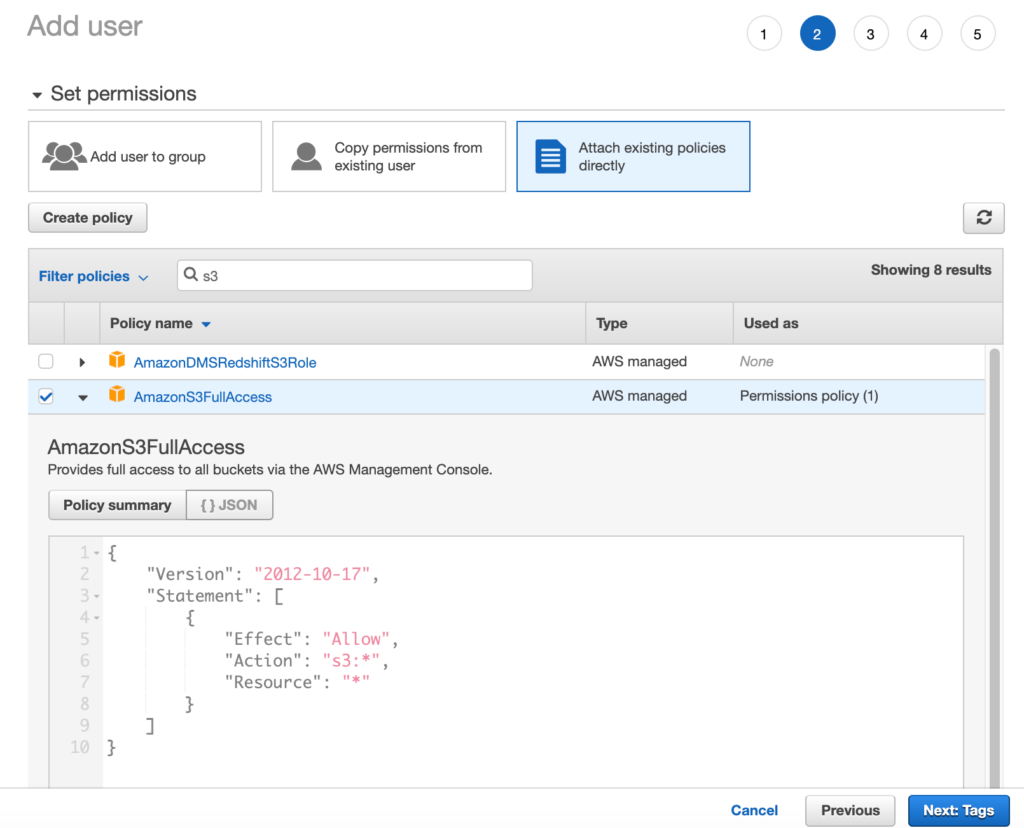
In the next screen that appears, select S3 from the filter and select AmazonS3FullAccess policy. This policy will grant the user full access to the buckets in the S3. You can also expand the policy summary to view the JSON policy that has been attached. Click Next: Tags and finally Create User. The user will receive an email to log in to the console and once logged in, the user can navigate to the S3 service and browse all the buckets under it.
Conclusion
In this article, we have learned about Identity and Access Management service available in the Amazon Web Services console. AWS IAM is an important service that allows administrators to control how resources or services within the account are accessed by other users. It also allows access control between two services so that there is no unnecessary access being granted. AWS provides us with a list of best practices that we should follow in order to keep our account safe and secure, the list can be found here. While designing IAM policies, the key is to grant the lease privileges to users and raise the access when required. Also, policies may be created and added to groups instead of individuals and users can then be added to those groups. This will reduce the work of adding separate permissions for each user.
Tags: amazon, AWS, cloud computing, cloud platform Last modified: October 26, 2022