Keeping credentials and other sensitive data out of application code can be a challenge. AWS Secrets Manager is meant to help abstract these data points all wrapped in a single easy-to-use service.
You pay a small amount per secret ($0.40) and an additional ($0.05) fee for every 1,000 requests to get those secrets. The entire process is TLS encrypted, and the service keeps the secrets safe.+
How to Create and Store the Secret
To get started with AWS Secrets Manager, you just need to have an AWS account. Search for Secrets Manager inside of the AWS console.
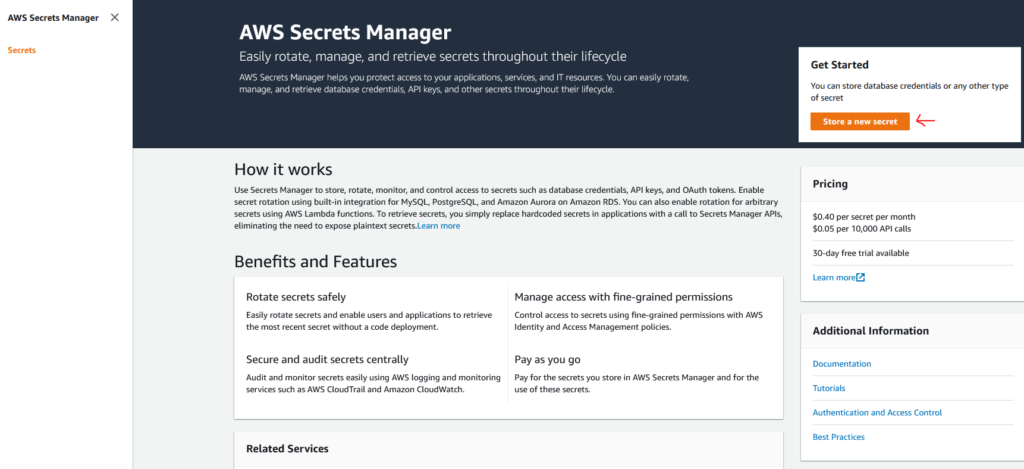
Navigate to the Secrets Manager Service and click Store a new secret
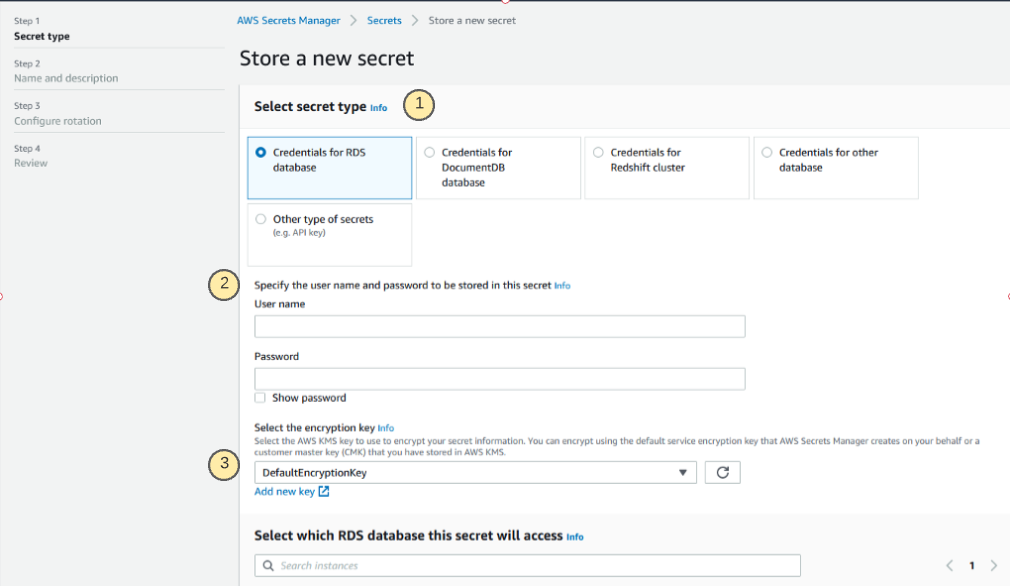
On the following screen, you will be prompted for the following:
- The type of secret that you are attempting to store. This can vary from database credentials of different kinds to key/value pairs that can be used for API keys or anything else.
- This section will deviate based on the selection of a secret type, these will be the values of the secrets which you are storing in the service.
- Encryption options can be customized with a user-defined encryption key. Default key is always available, too.
For this post I will be using Other as a secret type, this is a good option when you store API keys or other application credentials. Once the secret key/value fields are filled out, click Next.
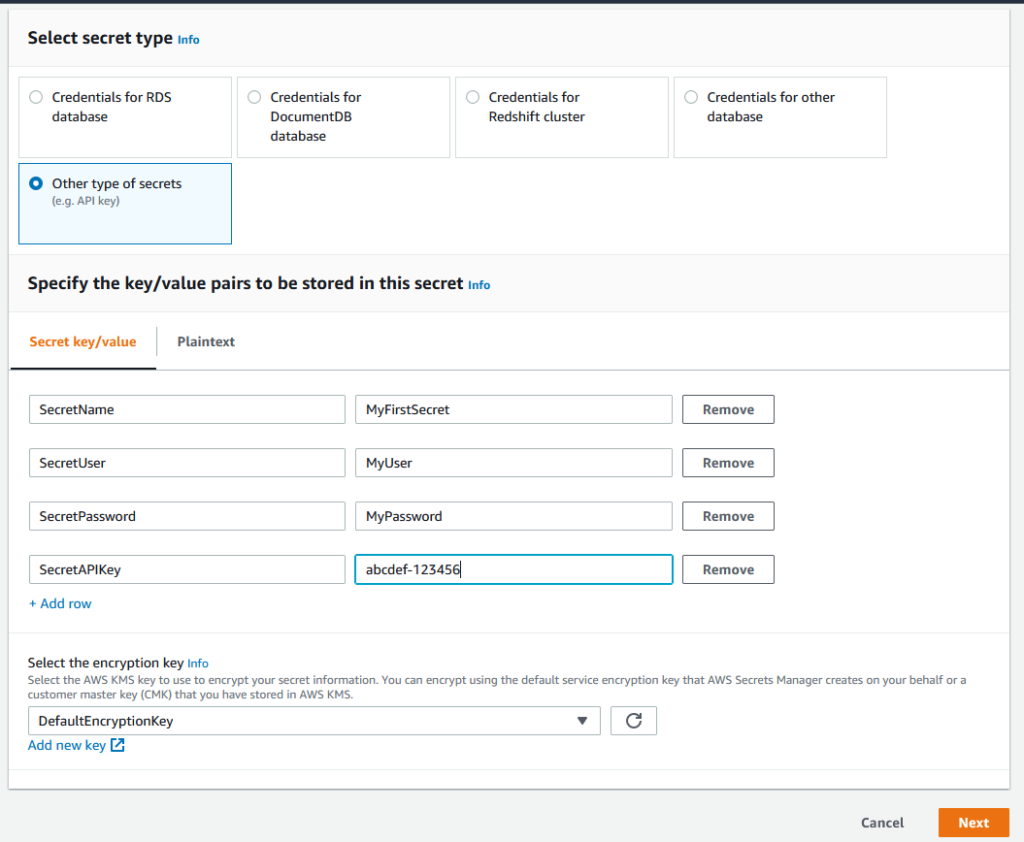
Give your secret a name and a description. It’s a good idea to follow a naming convention with something that mentions the environment and/or app name but the decision is up to you.
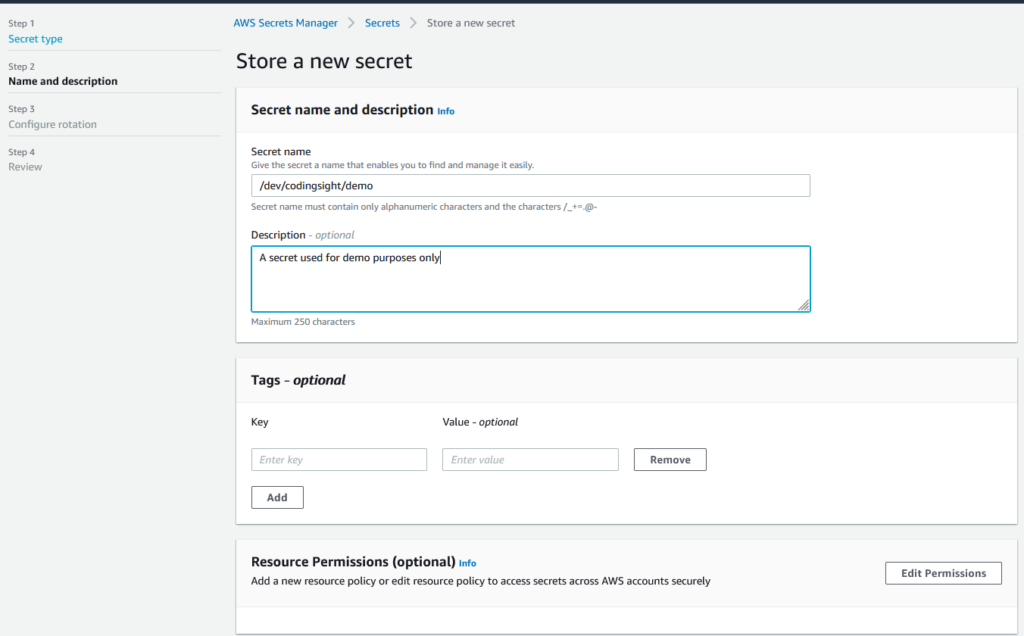
Click Next
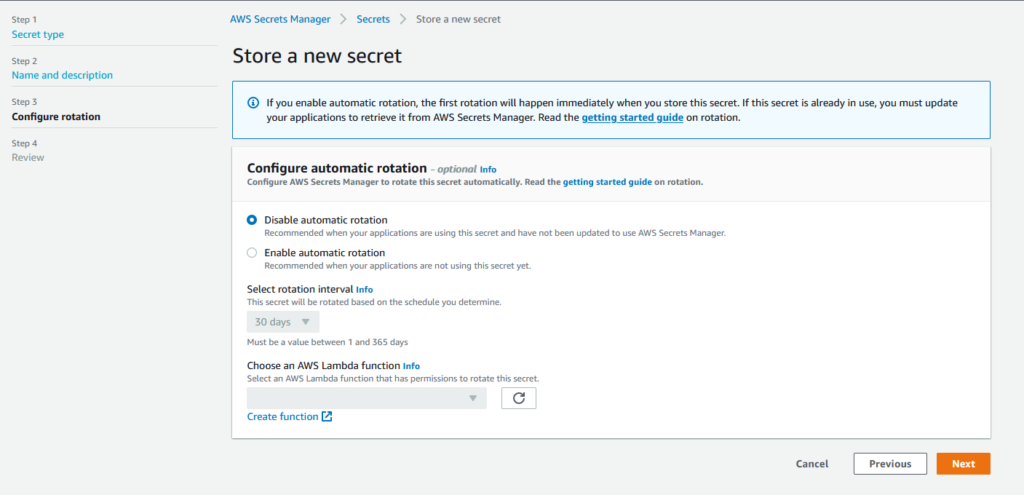
Secret Rotation
On the next screen, you can configure secret rotation. If you are using an AWS-hosted database, this secret rotation works seamlessly. It will automatically rotate the credentials of the RDS service with the given time frame. If you’re using it for other types of secrets, the rotation is still possible. But this would require a custom Lambda function to handle the rotating part.
For this demo, I will disable the automatic rotation. Click Next to review all options.
At the bottom of the review screen, you will see a section Sample Code. Here, you can choose a language, and the code required to retrieve your secrets will be generated.
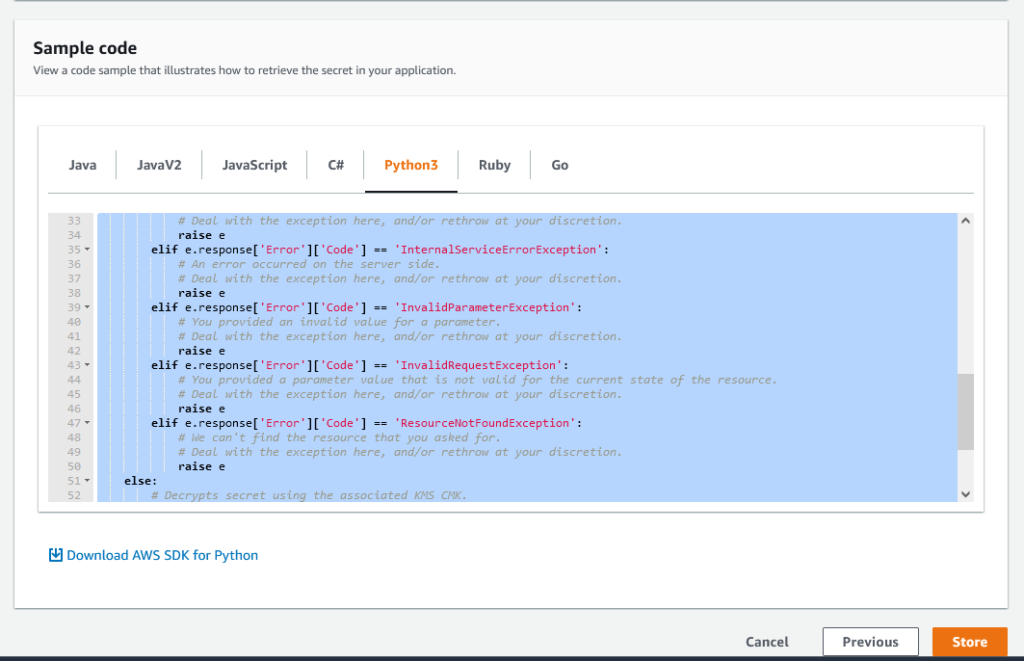
Click Store at the bottom of the review screen to store the secret.
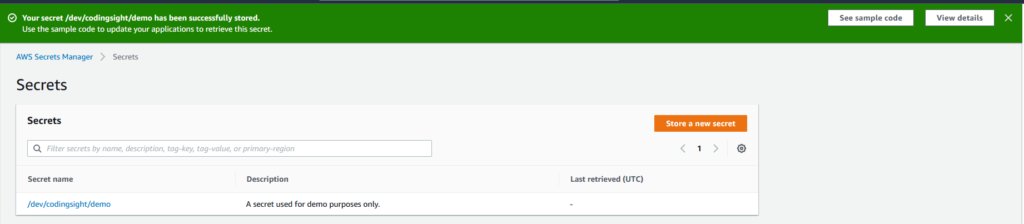
You should now see the secret when navigating to the Secrets Manager Service with the name and the description provided.
How to Check the Secret Values
The easiest way to check that your secret is configured and ready is to use the AWS CloudShell service. CloudShell is an AWS service that hosts a browser-based bash/command-line experience. This service will inherit the permission of the account that you are logged into. If you could create the secret, you will also be able to retrieve it with the CLI in CloudShell.
For this, we will utilize the AWS CLI command get-secret-value.
#Change /dev/codingsight/demo to your secret name
aws secretsmanager get-secret-value --secret-id /dev/codingsight/demo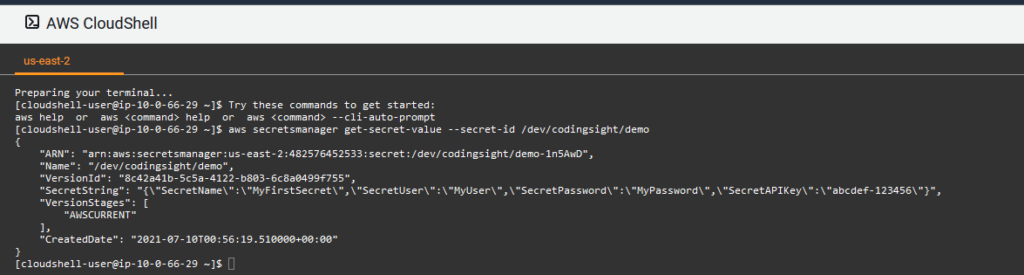
We can see that all the configured secret values are returning with this CLI call.
Retrieving Secret Values using Python
The next example will be through a Python script running on a local machine to retrieve the same values.
To do this, we will need certain permissions within the AWS account to read from Secret Manager. The exact IAM details around retrieving secrets can be found here. For this example, I will be using an access key and secret with an administrator privileges account.
Outside of the scope of this topic is configuring your machine for AWS command-line access. Through the boto3 framework, Python will pick up the configured key and secret. Boto3 will use the privileges assigned to that user to access the Secret Manager service.
Boto3 Script Example for AWS Secrets Manager
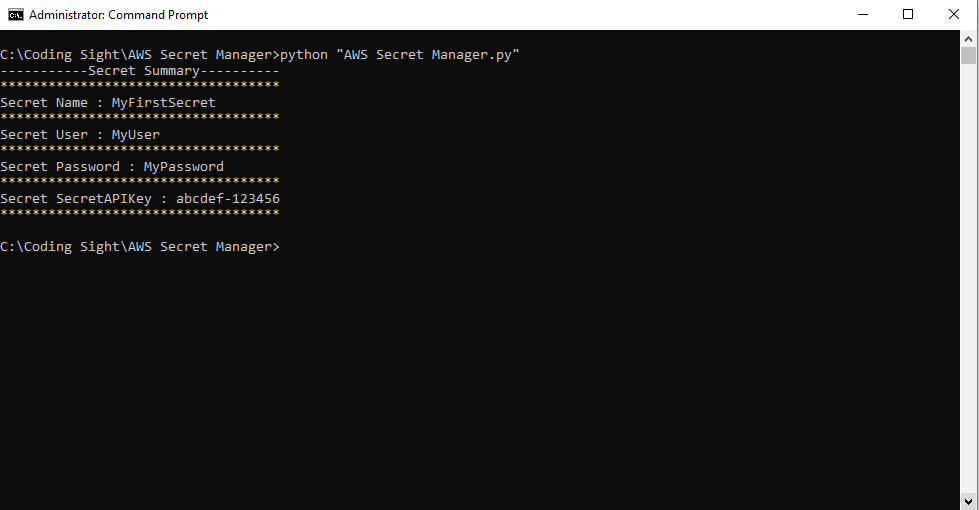
Using Python on a local machine, we can programmatically retrieve the secrets without hard coding anything within our Python script. Let’s take a look at the output of the Python script below AWS Secret Manager.py.
import boto3
import base64
from botocore.exceptions import ClientError
import json
def get_secret():
secret_name = "/dev/codingsight/demo" #change secret name
region_name = "us-east-2" #change region
session = boto3.session.Session()
client = session.client(
service_name='secretsmanager',
region_name=region_name
)
try:
get_secret_value_response = client.get_secret_value(
SecretId=secret_name
)
except ClientError as e:
if e.response['Error']['Code'] == 'DecryptionFailureException':
raise e
elif e.response['Error']['Code'] == 'InternalServiceErrorException':
raise e
elif e.response['Error']['Code'] == 'InvalidParameterException':
raise e
elif e.response['Error']['Code'] == 'InvalidRequestException':
raise e
elif e.response['Error']['Code'] == 'ResourceNotFoundException':
raise e
else:
if 'SecretString' in get_secret_value_response:
secret = get_secret_value_response['SecretString']
else:
decoded_binary_secret = base64.b64decode(get_secret_value_response['SecretBinary'])
return json.loads(secret)
s = get_secret()
print('-----------Secret Summary----------'+ '\n***********************************')
print('Secret Name : ' + s['SecretName'] + '\n***********************************')
print('Secret User : ' + s['SecretUser'] + '\n***********************************')
print('Secret Password : ' + s['SecretPassword'] + '\n***********************************')
print('Secret SecretAPIKey : ' + s['SecretAPIKey'] + '\n***********************************')
Summary
We discussed the advantages of using the AWS Secrets Manager service. They include not hard coding sensitive credentials in scripts and application code. We also demonstrated how to store and retrieve the Secrets Manager values from the cloud shell command line and with a Python script. AWS Secrets Manager is a great tool to help secure your applications and credentials.
Tags: AWS, secret manager Last modified: October 27, 2022









cheers.
I do not even know how I ended up here, but I thought this post was good. I don’t know who you are but certainly you’re going to a famous blogger if you aren’t already ? Cheers!